Breaking into a Locked Windows PC
- Published on
- Reading time
- 7 min read
Helping family break into their PCs
This post will be on the shorter side, but I wanted to jot down the steps I've recently taken to help a relative break into their PC. The process was recommended by a colleague, and it ended up being quite fun and educational. With the right tools, recovering a simple password can take seconds (hence why it's best to have more resilient security to prevent the exploit we'll explore). I'll tack on a few security recommendations at the end!
To set the stage, this PC had a single user locked out with no options to recover the account. The Windows filesystem was inaccessible, but I needed the encrypted version of the password. By booting Linux from a USB, the drive mounts to provide access to the hash, which can be matched against to find the password.
Sections
- Setting things up
- Finding the hashes
- Dictionary matching the password
- Wrapping up
- Security recommendations
Setting things up
For the USB distro, I recommend something lightweight. If you only plan on using it for this, get the smallest available. I used Ubuntu because that's what I've always used, but the download took longer than all other steps of the process combined. If you're keen to use Ubuntu as well, you can find their guide here! In summary:
- Download a bootable Ubuntu for USB
- Install Rufus
- In Rufus, navigate to your Ubuntu ISO file and write it to the USB
When ready, plug the drive into the locked PC and enter the boot menu. You can get there by pressing one of the F keys while the PC is powering on or restarting. Which F key depends on the computer, but the most common are F2, F10, and F12. When done correctly, the PC won't start normally and will instead open a screen with plain text.
The USB Linux should be detected automatically and appear as a boot option. Navigate to this using the arrow keys and press enter to start up in the new OS. This may take a few minutes, and a few set-up windows might pop up for you to click through.
Finding the hashes
When the set-up prompts are cleared out, use the terminal to locate the following files:
- C:\windows\system32\config\SAM
- C:\windows\system32\config\system
Dictionary matching the password
Next, install these two tools that will be used to dump and match the password's hash:
sudo apt update
sudo apt install samdump2
sudo apt install hashcat
samdump2 uses the syskey in the system file to access and dump the hashes stored in the SAM file. Run the following to extract them and store the ouput:
samdump2 -o output_file.txt system_file sam_file
hashcat will be used to guess and check for matching hashes. At this point, different attack modes can be considered depending on the password's complexity. For now, I'll do a dictionary attack, suitable for simple passwords where hashcat is provided a large txt file filled with common passwords to try. There are many such dictionaries available, but the one recommended to me is called rockyou. It can be downloaded here on Kaggle.
After picking one, the meat of the attack can begin. Fair warning, it can take a long time, and there is no guarantee of finding a match successfully. When ready, run the following command where output_file is either the file containing your hash or the hash itself:
hashcat -m 1000 -a 0 output_file rockyou.txt
-m 1000 sets the hashing algorithm to NTLM, which Windows used to create the original hash. It's important that these match; otherwise, the test won't be successful. -a 0 sets the attack mode to a dictionary attack. You can find a list of algorithms and attack modes here.
If set up correctly, the program should begin testing the passwords listed in rockyou.txt by hashing them with the specified algorithm and checking for a match. Each test's results will be displayed. When solved, the password and a status of Cracked will appear:
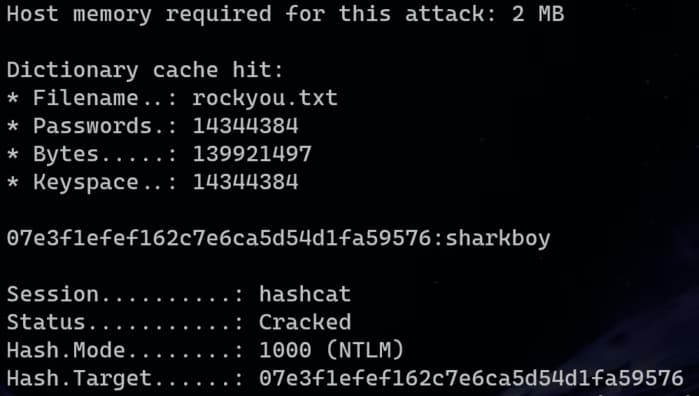
For the case above, hashcat cracked my test password by finding a hit in my cache. It was built on a previous run of this script to reduce future workload. Usually, the script will loop until finding a match, but mine cracked almost instantly by searching the existing cache first. Try testing something simple with only alphabetic characters to verify everything works. You can create an NTLM hash with iconv and openssl like this:
iconv -f ASCII -t UTF-16LE <(printf "lavagirl") | openssl dgst -md4 -provider legacy
Test the dictionary attack on the generated hash to be sure it cracks it successfully! If so, run this on the hash from the SAM file (ONLY if you own the device OR have direct permission to do so, of course). If this works, congratulations on recovering the password!
If it doesn't work or takes too long, larger dictionaries and/or other attack methods may yield better results. For example, when helping someone you know, you might be able to ask them what symbols exist in the password or what they remember about it. If they answer with something like, "Oh, it's two words separated by an exclamation point."; then you can test that pattern using a rule:
hashcat -m 1000 -a 1 A0B2D524A9C2A5C6DE2A7AA85F2CBF61 rockyou.txt rockyou.txt -j '$!'
-a 1 sets the attack mode to a combinator attack, named for the fact that we are combining different entries of rockyou.txt; provided twice to indicate the two dictionaries to pull words from and combine. -j '$!' appends an exclamation point to the end of the word in the first dictionary thus making a guess made up of two words separated by an ! (you can use -k to alter the words in the second dictionary).
Trying this rule-based attack as it is would take an unrealistic amount of time (my test estimated 70 days to crack 😅). Given what our example friend described, it is better to filter the password list to meet the criteria beforehand with a tool like grep. For example, if there are only lowercase letters, filter out all rockyou.txt entries containing other characters to reduce the keyspace.
Wrapping up
Exploring and testing different types of attacks can be a deep rabbit hole. In my case, I was lucky enough to crack the password with a basic dictionary attack. If you encounter a case where the script cannot return a match and your -a and -m are correct, it might be time to experiment with other attack modes that factor in context.
Rule-based attacks could prove successful, and there are also cases where hints given by the computer can help crack the password using an association attack (-a 9 in hashcat). But, as another word of caution, my family member's PC listed a hint that would have been a red herring as they informed me that it was outdated and irrelevant to their current password.
Security recommendations
Obviously, sharkboy and lavagirl are too simple to be passwords. Using a mix of numbers, uppercase characters, and symbols will decrease the likelihood of your password being cracked.
People often use simple passwords on their personal computers because they are not expecting anyone to gain access to their physical devices. If stolen, however, it will be simple for an attacker to break in and steal the information on the drive.
If someone gains access to your Windows device, enabling Secure Boot can help prevent some operating systems from gaining access, but this would ultimately just slow down an attacker. To ensure full protection, its best to keep backups of your files and put a mechanism in place to remotely wipe the hard drive. This way, you will be positioned to stop attackers without sacrificing personal data that is only stored on the compromised device.